Zama
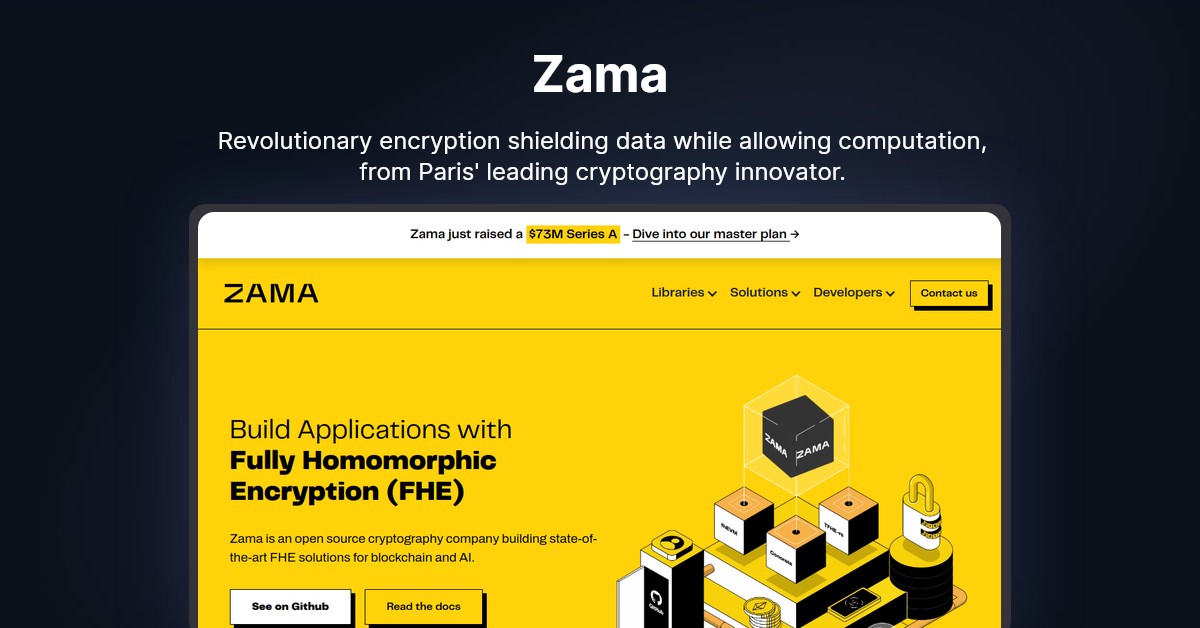
In today's digital age, privacy has become a pressing concern for individuals and businesses alike. With data breaches at an all-time high and surveillance becoming more invasive, the need for robust privacy solutions has never been more critical. Enter Zama, a pioneering cryptography company based in Paris, which is at the forefront of developing state-of-the-art fully homomorphic encryption (FHE) solutions. This revolutionary technology promises to transform the way we approach online privacy, making it possible to encrypt data end-to-end, regardless of where an application is running.
At the heart of Zama's mission is the development of open source homomorphic encryption tools designed for developers. But what exactly is fully homomorphic encryption, and how does it work? In essence, FHE allows for computations to be performed on encrypted data, without ever needing to decrypt it. This means that data can remain secure and private throughout the entire processing phase, a game-changer for privacy in the digital realm.
Zama's FHE solutions come packed with features designed to make privacy preservation accessible and straightforward. Embracing the open-source community, Zama ensures that their tools are available for everyone, fostering innovation and collaboration in the field of cryptography. With libraries and frameworks designed for ease of use, developers can integrate FHE into their applications without needing a deep understanding of the underlying cryptographic principles.
Highlights:
- Revolutionary fully homomorphic encryption technology
- Open source tools for developers
- End-to-end data encryption
- Versatile applications across multiple industries
- Enhanced privacy for individuals and businesses
Key Features:
- Concrete Framework for easy Python code conversion
- Low-level FHE operators in Rust for modular architecture
- Open source availability fostering innovation
- Easy integration for developers
- Versatile applications in blockchain, AI, and more
Benefits:
- Enhanced data privacy and security
- Compliance with privacy regulations
- Accessible for developers without deep cryptography knowledge
- Fostering innovation in the cryptography community
- Protection against data breaches and surveillance
Use Cases:
- Confidential credit scoring in financial institutions
- Preventive medicine with encrypted health information
- Enhanced biometric authentication privacy
- Tokenization and confidential trading in finance
- Onchain identity in blockchain applications
This content is either user submitted or generated using AI technology (including, but not limited to, Google Gemini API, Llama, Grok, and Mistral), based on automated research and analysis of public data sources from search engines like DuckDuckGo, Google Search, and SearXNG, and directly from the tool's own website and with minimal to no human editing/review. THEJO AI is not affiliated with or endorsed by the AI tools or services mentioned. This is provided for informational and reference purposes only, is not an endorsement or official advice, and may contain inaccuracies or biases. Please verify details with original sources.

Comments
Please log in to post a comment.