Phishing Risk Assessment Tool
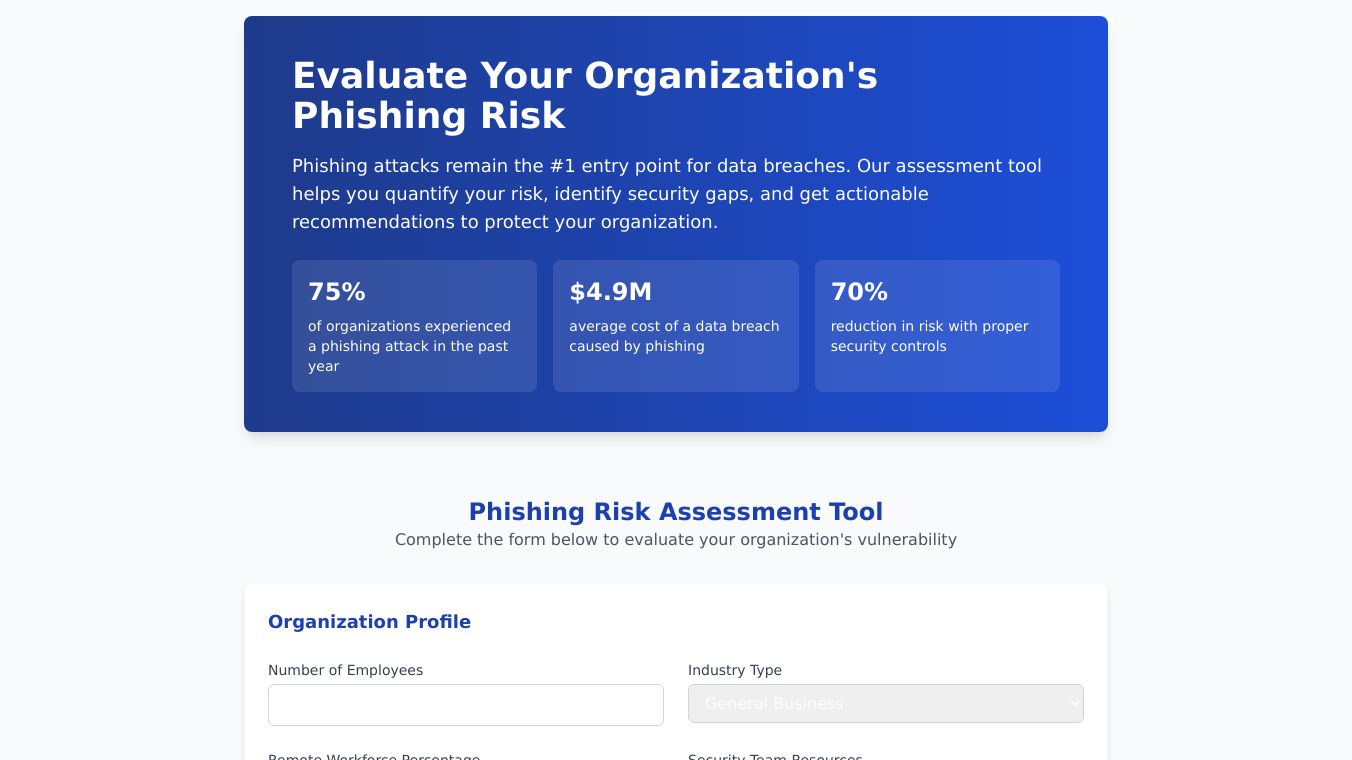
Phishing Risk Assessment Tool is a friendly web tool. It helps groups understand and lower the risks that come with phishing attacks. It gives a real time Phishing Risk Score. It does this by checking for breaches, leaks, and dark web data.
Benefits
The Phishing Risk Assessment Tool has many good points. It helps groups know their risk of being harmed by phishing attacks. Knowing this helps them take the right steps to boost their safety. The tool also makes a group''s security stronger by improving defenses against phishing attacks. Plus, it helps check and improve cybersecurity awareness among workers.
Use Cases
Different groups can use the Phishing Risk Assessment Tool. They can pretend to do phishing attacks and see how ready they are. This is very helpful for businesses that want to improve how aware and well trained their workers are. The tool is also great for finding weak spots and tracking security improvements over time.
Vibes
People like the Phishing Risk Assessment Tool because it gives clear data for good choices. The tool''s number based checks are liked more than word based ones. They give clear views of a group''s phishing risk.
Additional Information
The Phishing Risk Assessment Tool is part of a bigger plan to stop ransomware and other cyber threats. By doing regular checks and training, groups can greatly lower their risk of being harmed by phishing attacks.
This content is either user submitted or generated using AI technology (including, but not limited to, Google Gemini API, Llama, Grok, and Mistral), based on automated research and analysis of public data sources from search engines like DuckDuckGo, Google Search, and SearXNG, and directly from the tool's own website and with minimal to no human editing/review. THEJO AI is not affiliated with or endorsed by the AI tools or services mentioned. This is provided for informational and reference purposes only, is not an endorsement or official advice, and may contain inaccuracies or biases. Please verify details with original sources.
Comments
Please log in to post a comment.